Active Directory Deep Dive: The Complete Enterprise Identity Guide
Active Directory (AD) has been one of the most important core components of enterprise IT environments for more than twenty years.
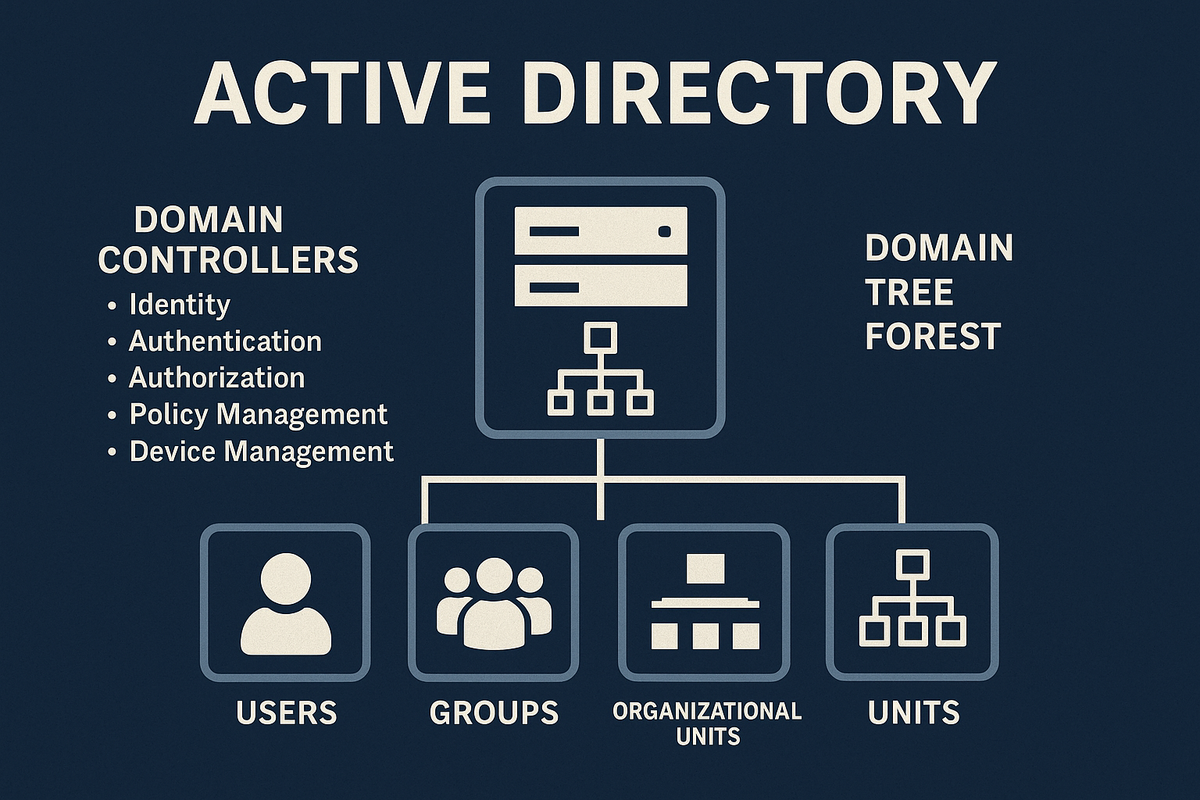
Active Directory (AD) has been one of the most important core components of enterprise IT environments for more than twenty years. Even as cloud-native identity platforms grow in popularity, traditional on-prem Active Directory remains the backbone of authentication, authorization, security, and device management in countless organizations.
This comprehensive guide explores how AD works, why it is still essential, and how to manage and secure it effectively in modern environments.
What Active Directory Actually Is
Active Directory is Microsoft’s enterprise-grade directory service. It provides:
- Identity management
- Access control
- Authentication
- Authorization
- Security policy enforcement
- Device and resource management
If AD becomes unavailable, users may be unable to log in, access resources, apply policies, or authenticate applications. AD is the organization’s identity control plane.
The Core Architecture: Domains, Trees, and Forests
Active Directory is structured in a hierarchical model designed for large and complex organizations.
Domain
A domain is the core administrative and security boundary. It contains:
- Users
- Computers
- Groups
- Policies
- Organizational Units
Tree
A collection of domains that share a contiguous namespace.
Automatic two-way trusts exist between domains in a tree.
Forest
A forest is the top-level identity boundary containing:
- One or more domain trees
- A shared schema
- Trust relationships
- Global catalog
The forest is the real security perimeter in AD.
Domain Controllers: The Heart of Active Directory
Domain Controllers (DCs) are the authoritative servers responsible for storing and managing the Active Directory database.
They handle:
- User authentication
- Kerberos ticket issuance
- Directory lookups (LDAP)
- Group Policy processing
- Replication between DCs
Proper Domain Controller design ensures:
- Redundancy
- Fault tolerance
- Fast authentication
- Consistent policy enforcement
A compromised DC equals a compromised entire domain.
Kerberos: How Authentication Works in AD
Active Directory uses Kerberos, a ticket-based authentication protocol, for secure and efficient identity verification.
- User logs in → receives a Ticket Granting Ticket (TGT)
- TGT is used to request service tickets
- Service tickets grant access to applications and resources
- No passwords are exchanged after login
Kerberos enables strong security and seamless Single Sign-On (SSO).
DNS: The Silent Backbone of AD
Active Directory depends heavily on DNS for:
- Domain Controller location
- Kerberos authentication
- LDAP endpoint discovery
- Replication
- Login operations
If DNS is misconfigured, AD fails instantly.
Most “AD issues” are actually DNS issues.
Organizational Units (OU): Structure and delegation
OUs allow you to organize:
- Departments
- Workstations
- Servers
- Admin scopes
- Policy islands
A well-designed OU structure enables:
- Scalable administration
- Clean GPO application
- Delegation without risk
- Consistent security enforcement
Group Policy: The Automation Engine of AD
Group Policy Objects (GPOs) are one of the most powerful enterprise tools. They enforce:
- Security settings
- Password and authentication rules
- Firewall configurations
- Software deployment
- OS hardening
- Registry settings
- Drive mappings
- Scripts
Properly managed GPOs maintain both security and stability across thousands of devices.
Users, Computers, and Service Accounts
User Accounts
Human identities used for authentication.
Computer Accounts
Machine identities for domain-joined devices.
Service Accounts
Used by applications and services.
Best practice: use gMSA (Group Managed Service Accounts) for automatic password rotation.
Trusts: Connecting Identity Boundaries
Active Directory supports several types of trust relationships:
- One-way / two-way
- Forest / external
- Transitive / non-transitive
- Selective authentication
Trusts determine which users can authenticate across domains or forests.
Replication: Keeping AD Data Consistent
Active Directory uses multi-master replication, meaning every Domain Controller can accept changes.
Replication is affected by:
- Sites and subnets
- Topologies
- Bridgehead servers
- Network latency
Administrators use tools like:
repadmindcdiag- Event logs
to validate health and replication.
Active Directory Security: Defending the Identity Core
AD is a high-value target for attackers. Common attack vectors include:
- Pass-the-Hash
- Kerberoasting
- Golden Ticket
- DCSync
- DCShadow
- LLMNR poisoning
- SMB relay attacks
Security best practices include:
- Tiered admin model
- Protected Users group
- LAPS for local admin passwords
- Disabling legacy protocols (NTLM, SMBv1)
- Enforcing strong Kerberos policies
- Hardening Domain Controllers
- Comprehensive auditing
Why Active Directory Still Dominates Today
Even in cloud-centric organizations, AD remains essential because it offers:
- Deep Windows ecosystem integration
- Enterprise-level policy enforcement
- Robust authentication mechanisms
- Support for legacy applications
- Hybrid identity capabilities
- Centralized governance
AD will continue to coexist with cloud IAM for many years.
Conclusion: AD Is Still the Identity Foundation of the Enterprise
Active Directory is not simply a user database — it is:
- The security perimeter
- The authentication engine
- The policy framework
- The device management hub
- The attacker’s ultimate target
Mastering AD means mastering enterprise identity itself.
For large organizations, there is no infrastructure component more critical than Active Directory.
