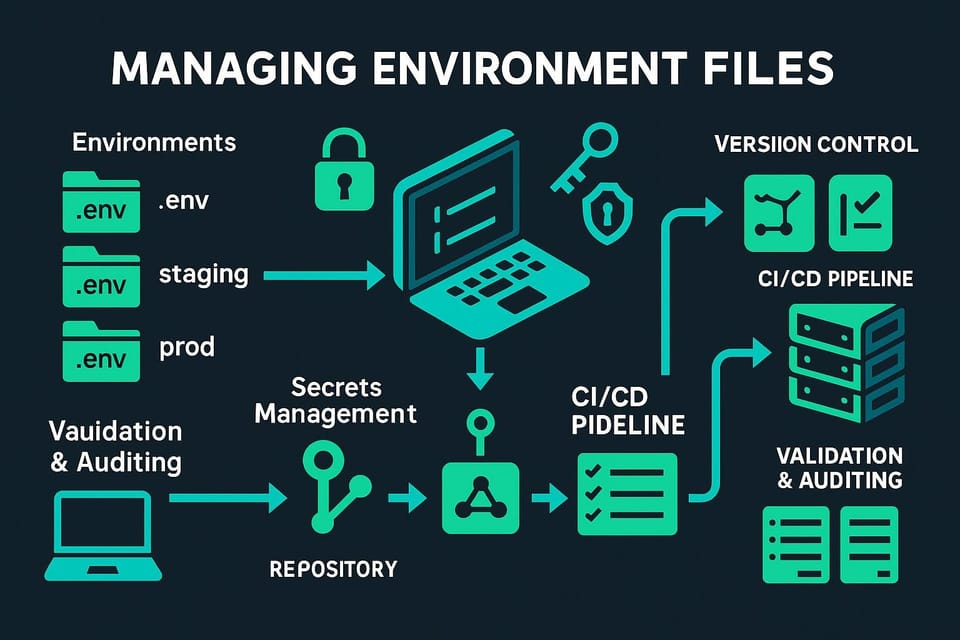
How to Achieve DevSecOps Integration
Enable teams to integrate development, security, and operations via automated pipelines, shared ownership, continuous feedback, and measurable security controls for faster delivery
Understanding the Critical Need for Security Integration in Modern Development
In today's rapidly evolving digital landscape, the separation between development, security, and operations has become not just inefficient but dangerously outdated. Organizations are discovering that bolting security onto finished products creates vulnerabilities that sophisticated attackers exploit with alarming regularity. The traditional approach of treating security as a final checkpoint before deployment has resulted in costly breaches, delayed releases, and a perpetual cycle of reactive fixes rather than proactive protection. This fundamental shift in how we build and deploy software isn't optional anymore—it's survival.
DevSecOps represents the seamless integration of security practices within the DevOps process, embedding protection mechanisms at every stage of the software development lifecycle rather than treating them as afterthoughts. This methodology transforms security from a bottleneck into an enabler, where automated checks, continuous monitoring, and shared responsibility create systems that are both agile and resilient. The promise here extends beyond mere compliance; it encompasses building trust with users, reducing technical debt, and creating development cultures where security becomes everyone's responsibility rather than a specialized team's burden.
Throughout this comprehensive guide, you'll discover practical strategies for implementing DevSecOps within your organization, regardless of your current maturity level. We'll explore the cultural transformations necessary for success, examine specific tools and technologies that facilitate integration, and provide actionable frameworks for measuring progress. You'll gain insights into overcoming common obstacles, understanding where to begin your journey, and building momentum that transforms security from obstacle to competitive advantage. Whether you're a developer seeking to expand your security knowledge, a security professional adapting to faster release cycles, or a leader orchestrating organizational change, this exploration will equip you with perspectives and tactics that translate directly into improved outcomes.
Establishing the Foundation: Cultural Transformation Before Technical Implementation
The most significant barrier to achieving genuine DevSecOps integration isn't technological—it's cultural. Organizations frequently invest in sophisticated security tools while maintaining organizational structures and mindsets that fundamentally contradict collaborative security practices. Development teams view security requirements as impediments to velocity, security professionals perceive developers as reckless risk-takers, and operations teams find themselves caught between competing pressures for both speed and stability. This tribalism creates environments where tools remain underutilized and processes become performative rather than protective.
Transforming this dynamic requires deliberate effort to build shared ownership across traditional boundaries. Leadership must articulate that security isn't the security team's exclusive domain but rather a collective responsibility where every role contributes specific expertise toward common objectives. This means developers need sufficient security training to identify vulnerabilities during coding, security professionals must understand development constraints and workflows, and operations teams require visibility into security metrics alongside performance indicators. The goal isn't creating security experts in every role but fostering enough literacy that teams speak a common language and appreciate interconnected impacts.
"Security cannot remain a separate function that reviews work after completion. When everyone owns security, it becomes woven into daily decisions rather than imposed through external judgment."
Practical steps toward cultural transformation include establishing cross-functional teams where security representatives participate in sprint planning and retrospectives rather than conducting isolated reviews. Implement blameless post-incident reviews that focus on systemic improvements rather than individual fault-finding. Create shared metrics that balance security outcomes with delivery speed, demonstrating that these objectives complement rather than contradict each other. Celebrate security wins as enthusiastically as feature releases, reinforcing that protection represents value creation rather than value prevention.
Education forms another critical pillar of cultural change. Developers benefit from training in secure coding practices, common vulnerability patterns, and the business impacts of security failures. Security teams gain value from understanding continuous integration/continuous deployment pipelines, infrastructure-as-code principles, and the pressures teams face to deliver rapidly. This mutual education shouldn't consist of occasional workshops but rather continuous learning integrated into regular workflows—pairing sessions, lunch-and-learns, internal documentation, and mentorship programs that make knowledge transfer organic rather than episodic.
Leadership commitment proves essential for sustaining cultural transformation beyond initial enthusiasm. When executives consistently prioritize security in resource allocation decisions, publicly support teams who delay releases to address vulnerabilities, and model collaborative behaviors across departmental boundaries, these signals permeate organizational culture far more effectively than policy documents. Conversely, when leaders treat security as negotiable during crunch periods or maintain rigid departmental hierarchies, teams quickly recognize the gap between stated values and operational reality, undermining integration efforts regardless of technical investments.
Building Trust Through Transparent Communication
Transparency serves as the lubricant for cross-functional collaboration, yet many organizations maintain information silos that prevent effective DevSecOps integration. Security teams often withhold vulnerability details fearing they'll be deprioritized, while development teams avoid discussing technical debt that might attract security scrutiny. This mutual concealment creates environments where problems fester until they become crises, reinforcing adversarial dynamics rather than partnership.
Establishing transparent communication channels requires creating safe spaces for difficult conversations. Regular security forums where teams discuss vulnerabilities without judgment, shared dashboards that make security metrics visible to all stakeholders, and documented decision-making processes that explain trade-offs all contribute to environments where information flows freely. When teams understand the reasoning behind security requirements and security professionals appreciate delivery constraints, negotiations become collaborative problem-solving rather than positional bargaining.
Selecting and Implementing the Right Technology Stack
While culture provides the foundation, appropriate technology enables DevSecOps practices to scale beyond individual heroics. The modern security tooling landscape offers overwhelming options, and organizations frequently accumulate tools that generate more noise than insight. Effective technology selection requires understanding your specific context—development languages, deployment patterns, risk profile, and team capabilities—rather than adopting whatever appears in trending vendor comparisons.
A comprehensive DevSecOps technology stack addresses security across the entire development lifecycle, from initial coding through production monitoring. Static Application Security Testing (SAST) tools analyze source code for vulnerabilities before execution, identifying issues like SQL injection risks, cross-site scripting vulnerabilities, and insecure authentication patterns. These tools integrate directly into development environments and continuous integration pipelines, providing immediate feedback that enables developers to address issues while context remains fresh. The key to SAST effectiveness lies in careful tuning to reduce false positives that train developers to ignore warnings.
Dynamic Application Security Testing (DAST) tools complement static analysis by testing running applications, simulating attacker techniques against deployed systems to identify vulnerabilities that only manifest during execution. Unlike SAST, which examines code structure, DAST evaluates actual application behavior, catching configuration errors, runtime vulnerabilities, and issues arising from component interactions. Implementing DAST requires test environments that accurately mirror production configurations, as discrepancies between testing and production environments create blind spots where vulnerabilities hide.
| Security Testing Approach | Lifecycle Stage | Primary Strengths | Common Limitations | Integration Points |
|---|---|---|---|---|
| Static Analysis (SAST) | Development/Commit | Early detection, comprehensive code coverage, no runtime required | High false positive rates, limited runtime context, language-specific | IDE plugins, pre-commit hooks, CI pipeline stages |
| Dynamic Analysis (DAST) | Testing/Staging | Real-world attack simulation, configuration testing, runtime behavior | Requires running application, limited code coverage, slower execution | Automated test suites, staging deployments, scheduled scans |
| Interactive Analysis (IAST) | Testing/Staging | Low false positives, precise vulnerability location, real-time feedback | Requires instrumentation, performance overhead, environment-specific | Application servers, testing frameworks, monitoring systems |
| Software Composition Analysis (SCA) | Development/Build | Dependency vulnerability detection, license compliance, supply chain visibility | Database currency, transitive dependency complexity, remediation guidance | Package managers, build tools, dependency management systems |
| Runtime Protection (RASP) | Production | Real-time threat blocking, zero-day protection, attack intelligence | Performance impact, false positive disruption, implementation complexity | Application frameworks, web servers, container orchestration |
Software Composition Analysis (SCA) tools address the reality that modern applications consist primarily of third-party components and open-source libraries. These tools inventory dependencies, identify known vulnerabilities in those components, and often provide guidance on remediation through updates or alternatives. Given that vulnerabilities in dependencies represent a substantial portion of application security risks, SCA integration into build processes ensures teams maintain awareness of their supply chain security posture. Effective SCA implementation requires policies for addressing identified vulnerabilities—which severity levels block builds, acceptable timeframes for remediation, and processes for handling components without available fixes.
"The best security tool is the one your team actually uses consistently. Sophisticated capabilities mean nothing if friction prevents adoption or alert fatigue causes teams to ignore findings."
Container security scanning has become essential as containerization dominates modern deployment patterns. These tools analyze container images for vulnerabilities in base images, installed packages, and configuration weaknesses. Integration points include image registries that prevent vulnerable images from being pulled, CI pipelines that scan images during build processes, and runtime monitoring that detects anomalous container behavior. Container security extends beyond vulnerability scanning to encompass image provenance verification, ensuring that deployed containers match approved sources and haven't been tampered with during distribution.
Infrastructure-as-code security scanning evaluates configuration files for cloud resources, Kubernetes deployments, and infrastructure definitions before they're applied to environments. These tools identify misconfigurations like overly permissive access policies, unencrypted storage, publicly exposed services, and compliance violations. By catching infrastructure security issues before deployment, teams avoid the costly cycle of deploying insecure configurations and then scrambling to remediate them in production. This proactive approach proves particularly valuable in cloud environments where misconfigurations can expose sensitive data or create unexpected costs.
Orchestrating Tools Through Pipeline Integration
Individual security tools provide value, but their real power emerges through orchestrated integration within CI/CD pipelines. This integration transforms security from manual checkpoints into automated gates that provide consistent enforcement without human bottlenecks. Pipeline integration requires careful consideration of where each tool operates most effectively and how findings translate into actionable workflow steps.
Early pipeline stages incorporate fast-running checks that provide immediate feedback—static analysis on changed code, commit message validation, and secret scanning that prevents credentials from entering repositories. Middle stages run more comprehensive analyses as code moves through build processes—full SAST scans, dependency vulnerability checks, and container image scanning. Later stages before production deployment include DAST scans against staging environments, infrastructure configuration validation, and compliance verification. This layered approach balances speed with thoroughness, catching obvious issues quickly while reserving time-intensive analysis for code that has passed initial quality gates.
Effective pipeline integration requires thoughtful handling of security findings to avoid either blocking legitimate deployments or allowing vulnerabilities to reach production. Implement severity-based policies where critical vulnerabilities block deployments automatically, high-severity issues generate alerts requiring explicit acknowledgment, and lower-severity findings create tickets for future remediation without blocking current releases. This nuanced approach maintains velocity while ensuring serious risks receive immediate attention. Regularly review and adjust these thresholds based on your organization's risk tolerance and the accuracy of tool findings in your specific context.
Implementing Continuous Security Monitoring and Response
DevSecOps integration doesn't conclude when code reaches production; rather, production environments represent critical security monitoring opportunities. Traditional security models treated production as a relatively static environment requiring periodic assessment, but modern deployment practices with frequent updates and dynamic infrastructure demand continuous monitoring and rapid response capabilities. Production security monitoring provides visibility into actual attack attempts, identifies vulnerabilities that testing missed, and generates intelligence that improves earlier development stages.
Runtime application self-protection (RASP) technologies embed security monitoring and enforcement directly within running applications, enabling real-time detection and blocking of attacks. Unlike perimeter-based security that attempts to filter malicious traffic before it reaches applications, RASP operates with full application context, distinguishing between legitimate and malicious requests based on actual application behavior rather than pattern matching. This context awareness dramatically reduces false positives while catching sophisticated attacks that evade traditional web application firewalls.
Log aggregation and security information event management (SIEM) systems collect security-relevant data from across infrastructure and applications, enabling correlation analysis that identifies attack patterns invisible when examining individual systems. Effective SIEM implementation requires careful consideration of what to log—capturing sufficient detail for security analysis without overwhelming storage and analysis capabilities. Focus on security-relevant events like authentication attempts, authorization failures, data access patterns, configuration changes, and anomalous network connections rather than attempting to log everything indiscriminately.
"Monitoring without response is merely expensive observation. The value comes from translating detected anomalies into rapid, appropriate actions that contain threats before they cause damage."
Anomaly detection leverages machine learning to establish baselines of normal application and infrastructure behavior, then alerting on deviations that might indicate security incidents. This approach proves particularly valuable for detecting novel attacks that don't match known signatures and identifying compromised credentials being used in unusual patterns. However, anomaly detection requires careful tuning and ongoing refinement as application behavior evolves, otherwise alert fatigue from false positives undermines its effectiveness.
Incident response processes must adapt to DevSecOps velocity, moving beyond monthly tabletop exercises to continuous improvement integrated with regular operations. Automated incident response playbooks can execute initial containment actions—isolating affected systems, revoking potentially compromised credentials, capturing forensic data—while human responders assess situations and determine appropriate next steps. This automation proves essential when incidents occur outside business hours or when response speed determines the difference between minor incidents and major breaches.
Establishing Feedback Loops from Production to Development
Production security insights should inform development practices, creating feedback loops that continuously improve application security. When production monitoring detects attack attempts exploiting specific vulnerability classes, that intelligence should translate into enhanced testing for similar issues in development. Patterns of configuration errors in production should trigger infrastructure-as-code template improvements. Performance impacts from security controls should drive optimization efforts that maintain protection without degrading user experience.
Implementing these feedback loops requires breaking down organizational barriers between production operations and development teams. Regular cross-functional reviews of security incidents, shared dashboards displaying production security metrics to development teams, and rotation programs where developers participate in on-call incident response all create connections that translate production learning into development improvements. These mechanisms transform security from a series of isolated checkpoints into a continuous learning system that becomes more effective over time.
Measuring Progress and Demonstrating Value
Effective DevSecOps integration requires metrics that demonstrate progress and guide improvement efforts. However, security metrics frequently fall into traps of measuring activity rather than outcomes or focusing on lagging indicators that provide little actionable guidance. Thoughtful metric selection balances leading indicators that enable proactive improvement with outcome measures that demonstrate actual security posture improvements.
📊 Mean time to remediate vulnerabilities measures how quickly identified security issues move from discovery to resolution, providing insight into both process efficiency and prioritization effectiveness. Track this metric separately for different severity levels, as treating all vulnerabilities identically obscures whether critical issues receive appropriate urgency. Declining remediation times indicate improving processes, while increasing times signal bottlenecks requiring attention. This metric proves more valuable than simple vulnerability counts, which can increase as security testing improves without indicating worsening security posture.
🔍 Security test coverage quantifies what portion of code, infrastructure, and dependencies undergoes security analysis. This includes code coverage for SAST tools, API endpoint coverage for DAST testing, and dependency analysis completeness. Improving coverage often yields more security value than adding additional tool types, as comprehensive analysis with existing tools typically identifies more issues than superficial analysis with a broader tool portfolio. Track coverage trends over time and investigate coverage gaps that might indicate blind spots in security practices.
⚡ Security issue escape rate measures what percentage of security vulnerabilities reach production despite earlier testing, indicating the effectiveness of pre-production security controls. Calculate this by comparing production-discovered vulnerabilities to total vulnerabilities identified across all stages. High escape rates suggest gaps in testing coverage, inadequate test environment fidelity, or tool configuration issues that prevent detection of certain vulnerability classes. This metric provides valuable feedback for improving earlier security testing.
| Metric Category | Specific Measurements | What It Reveals | Improvement Actions |
|---|---|---|---|
| Velocity Impact | Build time increase from security scans, deployment frequency changes, lead time for changes | Whether security integration maintains development speed or creates bottlenecks | Tool optimization, policy refinement, automation enhancement, parallel processing |
| Detection Effectiveness | Vulnerabilities found per stage, false positive rates, coverage percentages, tool accuracy | How well security testing identifies real issues without excessive noise | Tool tuning, additional tool types, enhanced test environments, coverage expansion |
| Response Efficiency | Mean time to detect, mean time to remediate, remediation backlog size, SLA compliance | How quickly identified issues move to resolution | Process streamlining, prioritization improvement, resource allocation, automation |
| Risk Reduction | Open vulnerability trends, severity distribution, attack surface changes, incident frequency | Whether overall security posture improves over time | Proactive security activities, architectural improvements, control effectiveness review |
| Cultural Adoption | Security training completion, cross-functional collaboration instances, security champions participation | Whether security mindset permeates organization beyond specialist roles | Education programs, incentive alignment, leadership messaging, recognition programs |
🛡️ Security debt quantifies the accumulated burden of known but unaddressed security issues, analogous to technical debt. Track both the absolute number of open security issues and trends over time, categorized by severity and age. Growing security debt indicates that vulnerability discovery outpaces remediation, requiring either increased remediation capacity or more aggressive prioritization. Like technical debt, some security debt may be acceptable if consciously acknowledged and managed, but uncontrolled accumulation eventually creates crises.
🎯 Deployment success rate measures what percentage of deployments complete without security-related rollbacks or emergency patches. This metric reveals whether security controls effectively prevent vulnerable code from reaching production without creating excessive false alarms that block legitimate releases. Declining success rates might indicate overly aggressive security policies, while very high rates combined with production security incidents suggest insufficiently stringent controls.
"Metrics should drive improvement conversations, not blame assignment. When teams fear measurement, they game metrics rather than improving underlying practices."
Beyond quantitative metrics, qualitative assessments provide valuable context for understanding DevSecOps maturity. Regular surveys assessing team confidence in security practices, perceived friction from security requirements, and cross-functional relationship quality reveal cultural factors that quantitative metrics miss. Security incident retrospectives that examine not just technical failures but also process and communication breakdowns identify improvement opportunities that metrics alone wouldn't surface.
Communicating metrics effectively requires tailoring presentations to different audiences. Executives need high-level trends demonstrating risk reduction and business value, development teams benefit from actionable metrics showing where to focus improvement efforts, and security teams require detailed breakdowns enabling tool and process optimization. Avoid metric proliferation that overwhelms audiences; instead, establish a core set of key indicators supplemented by detailed metrics available for deeper investigation when needed.
Overcoming Common Implementation Challenges
DevSecOps integration encounters predictable obstacles that derail initiatives if not addressed proactively. Understanding these challenges and proven mitigation strategies increases the likelihood of successful transformation. Many organizations cycle through repeated failed attempts because they don't learn from common pitfalls that have trapped others.
Alert fatigue represents one of the most pervasive challenges, where security tools generate such high volumes of findings that teams become desensitized and ignore warnings, including legitimate critical issues. This typically results from inadequate tool tuning, attempting to address all findings simultaneously regardless of severity, and lack of contextual filtering that distinguishes findings relevant to specific applications. Combat alert fatigue through aggressive false positive reduction, severity-based prioritization that focuses attention on critical issues, and contextual suppression that filters findings based on application-specific factors like whether vulnerable code paths are actually exposed.
Tool sprawl occurs when organizations accumulate security tools without integrating them into coherent workflows, creating overlapping capabilities, inconsistent findings, and management overhead that consumes resources without proportional security improvements. This often stems from point solutions addressing specific gaps without considering overall architecture, vendor relationships that bundle tools regardless of need, and lack of governance over tool acquisition. Address tool sprawl through periodic tool portfolio reviews, consolidation where multiple tools provide similar capabilities, and standardization on platforms that integrate multiple security functions rather than maintaining separate point solutions.
"Starting with comprehensive tool deployment across all areas simultaneously overwhelms teams and guarantees failure. Progressive implementation that demonstrates value before expanding scope builds momentum and organizational buy-in."
Skills gaps create situations where organizations invest in sophisticated security capabilities but lack personnel who can effectively operate them. Developers may lack security expertise to interpret findings and implement proper remediations, security professionals might not understand modern development practices sufficiently to integrate smoothly, and operations teams may struggle with security tool management. Bridge skills gaps through cross-training programs, embedded security champions within development teams, external training investments, and hiring strategies that prioritize learning ability over current expertise in rapidly evolving domains.
Legacy system integration challenges arise when attempting to apply modern DevSecOps practices to applications built before these methodologies existed. Legacy systems often lack automated testing, use outdated languages unsupported by modern security tools, and have architectures that complicate security analysis. Approach legacy systems pragmatically by focusing security efforts on integration points where legacy systems interact with modern components, implementing compensating controls like runtime protection when source code analysis isn't feasible, and using legacy system modernization efforts as opportunities to introduce security practices rather than attempting wholesale transformation of stable legacy environments.
Compliance and audit friction emerges when traditional compliance frameworks designed for waterfall development clash with continuous deployment practices. Auditors accustomed to reviewing security at defined gates struggle with security integrated throughout pipelines, and compliance documentation requirements designed for infrequent releases become burdensome with daily deployments. Address this through educating auditors on DevSecOps practices, implementing continuous compliance monitoring that provides audit evidence automatically, and working with compliance teams to reframe requirements in terms of outcomes rather than specific processes, allowing flexibility in how security objectives are achieved.
Building Momentum Through Quick Wins
Successful DevSecOps integration requires demonstrating value early to build organizational support for continued investment. Identify quick wins that provide visible security improvements without extensive implementation effort—secret scanning to prevent credential exposure, dependency vulnerability scanning that identifies easily remediable issues, or automated security testing for new projects while legacy applications follow existing processes. These early successes create positive momentum and provide learning opportunities that inform broader rollout.
Celebrate and communicate quick wins broadly, ensuring that leadership, development teams, and security professionals all recognize progress. This visibility builds confidence that DevSecOps integration delivers tangible value rather than merely creating additional process overhead. Use early successes to secure resources for more ambitious initiatives, demonstrating that security investments generate returns rather than simply consuming budgets.
Scaling DevSecOps Across the Organization
Initial DevSecOps implementation often begins with pilot projects or individual teams, but realizing full value requires scaling practices across the entire organization. This scaling presents distinct challenges from initial implementation, as approaches that worked for early adopters may not transfer directly to teams with different contexts, and consistency becomes important to avoid creating fragmented security postures.
Security champions programs distribute security expertise throughout the organization by identifying and empowering individuals within development teams who have both security interest and peer credibility. These champions serve as initial points of contact for security questions, advocate for security practices within their teams, and provide feedback to central security teams about what's working and what's creating friction. Effective champion programs provide regular training, create communities where champions share experiences, and recognize contributions to maintain engagement. This distributed model scales security expertise more effectively than attempting to embed dedicated security professionals in every team.
Platform teams create reusable security capabilities that application teams consume without reimplementing security controls repeatedly. These platforms might include hardened container base images, pre-configured CI/CD pipeline templates with integrated security scanning, infrastructure-as-code modules for common secure configurations, and shared libraries for authentication and authorization. By centralizing security implementation in platforms, organizations achieve consistency while allowing application teams to focus on business logic rather than security infrastructure. Platform approaches require treating internal teams as customers, prioritizing usability and support to drive adoption.
Progressive policy enforcement recognizes that different applications require different security rigor based on their risk profiles, while maintaining minimum standards across all systems. Classify applications based on data sensitivity, exposure level, and business criticality, then define appropriate security requirements for each classification. High-risk applications might require comprehensive security testing and manual review before production deployment, while low-risk internal tools follow streamlined processes. This risk-based approach focuses security resources where they provide maximum value rather than applying uniform requirements regardless of context.
"Scaling requires balancing consistency with flexibility. Overly rigid standardization creates rebellion, while excessive flexibility fragments security posture and prevents learning across teams."
Inner source security practices apply open source collaboration models internally, allowing teams to contribute improvements to shared security tools, documentation, and practices. When a team develops an effective solution to a common security challenge, inner source approaches enable other teams to adopt and adapt that solution rather than solving the same problem repeatedly. This collaborative model accelerates learning and improvement while building cross-team relationships that support cultural integration. Implement inner source through internal repositories for security tools and configurations, contribution guidelines that welcome improvements, and recognition for teams that share valuable solutions.
Federated security governance distributes security decision-making appropriately while maintaining overall coherence. Central security teams establish principles, standards, and minimum requirements, but individual teams have autonomy in how they meet those requirements within their specific contexts. This federated approach prevents central bottlenecks while ensuring consistent security outcomes. Regular forums where teams share approaches and challenges create learning opportunities and identify where additional standardization would provide value versus where diversity reflects legitimate contextual differences.
Adapting to Emerging Technologies and Threats
DevSecOps practices must evolve continuously as both technology landscapes and threat environments change. Approaches that effectively secured applications five years ago may prove inadequate for modern architectures, and threat actors constantly develop new techniques that exploit emerging vulnerabilities. Building adaptability into DevSecOps practices ensures they remain effective despite inevitable change.
Cloud-native security requires rethinking traditional perimeter-focused security for environments where application components distribute across multiple services, infrastructure is ephemeral and constantly changing, and traditional network boundaries don't exist. Cloud-native security emphasizes identity and access management over network controls, immutable infrastructure that prevents runtime modification, and comprehensive logging that enables forensic analysis in distributed environments. DevSecOps practices for cloud-native applications must integrate security into infrastructure-as-code, implement service mesh security for microservice communication, and leverage cloud provider security services rather than attempting to replicate on-premises security models.
Serverless security addresses unique challenges in environments where application code runs in managed execution environments without traditional servers. Serverless applications require security focus on function-level permissions, dependency management for function packages, secure configuration of event sources and triggers, and monitoring of function invocations for anomalous behavior. Traditional security approaches like host hardening and network segmentation don't apply, requiring new techniques specific to serverless architectures. DevSecOps practices must adapt security testing to evaluate function code and configurations, implement least-privilege permissions for each function, and monitor for security-relevant events in serverless environments.
Supply chain security has gained prominence as attacks targeting software supply chains demonstrate devastating impact. DevSecOps must address security throughout the software supply chain, from development tool integrity through build process security to deployment artifact verification. Implement software bill of materials (SBOM) generation that documents all components in deployed applications, artifact signing that ensures deployed code matches approved sources, and build process attestation that provides verifiable evidence of security controls during building. These practices provide transparency and verification that detect supply chain compromises before they reach production.
AI and machine learning security presents emerging challenges as organizations increasingly incorporate AI/ML models into applications. These models introduce unique vulnerabilities including adversarial inputs that manipulate model behavior, training data poisoning, and model theft through inference attacks. DevSecOps practices must expand to include model security testing, training data validation, and monitoring for adversarial attacks against deployed models. As AI/ML becomes ubiquitous in applications, security practices that don't address these unique risks leave significant blind spots.
"The only constant in technology is change. DevSecOps practices must incorporate continuous learning and adaptation as core principles rather than treating security as a solved problem with static solutions."
Maintaining awareness of emerging threats requires establishing threat intelligence feeds, participating in security communities, and conducting regular threat modeling exercises that consider how evolving attack techniques might impact your specific applications and infrastructure. Allocate time for security teams to research emerging threats and experiment with new security technologies, ensuring your practices evolve proactively rather than reactively after incidents expose gaps. Build relationships with security researchers and participate in vulnerability disclosure programs that provide early warning of issues affecting your technology stack.
Creating Sustainable DevSecOps Practices
Long-term DevSecOps success requires building sustainable practices that persist beyond initial implementation enthusiasm. Many organizations experience initial progress followed by gradual erosion as attention shifts to other priorities, security practices become outdated, or key individuals leave. Sustainability requires embedding DevSecOps into organizational DNA rather than treating it as a temporary initiative.
Documentation and knowledge management preserve institutional knowledge about security practices, tool configurations, and lessons learned from incidents. Comprehensive documentation enables new team members to onboard effectively, provides references when questions arise, and creates shared understanding across teams. However, documentation requires continuous maintenance to remain valuable as practices evolve. Implement documentation as code, storing it in version control alongside application code and infrastructure definitions, and treat documentation updates as required components of changes rather than optional afterthoughts. Create templates for common documentation needs like security architecture decisions, incident response playbooks, and tool configuration guides to reduce documentation effort and improve consistency.
Continuous improvement processes ensure DevSecOps practices evolve based on experience rather than stagnating at initial implementation. Regular retrospectives examining security incidents, near-misses, and process friction identify improvement opportunities. Establish forums where teams share experiences and challenges, enabling cross-pollination of effective practices. Track metrics over time to identify trends requiring attention. Allocate dedicated time for improvement work rather than expecting it to happen opportunistically amid feature development pressure. Treat security practice improvement as valuable work deserving explicit prioritization rather than something that happens only when convenient.
Security champions succession planning addresses the risk that DevSecOps practices depend too heavily on specific individuals whose departure would significantly impact capabilities. Identify potential champions early and provide development opportunities that prepare them for expanded security roles. Document champion responsibilities and knowledge so transitions don't require starting from scratch. Create communities of champions where knowledge sharing prevents isolation and builds redundancy. Recognize and reward champion contributions to maintain motivation and demonstrate that security work represents valuable career development rather than unrewarded extra effort.
Budget and resource stability prevents the boom-bust cycles where security initiatives receive significant investment during crises then face cuts when immediate threats recede. Establish security as ongoing operational investment rather than project-based funding that expires. Build security costs into standard development budgets rather than maintaining separate security budgets that become easy targets during cost reduction efforts. Demonstrate security value through metrics that connect security investments to business outcomes, making the case for continued funding based on demonstrated returns rather than fear-based arguments about potential breaches.
Executive engagement maintains leadership attention and support beyond initial implementation. Regular executive briefings on security posture, emerging threats, and improvement initiatives keep security visible at leadership levels. Include security metrics in standard business reviews alongside other operational indicators. Engage executives in security exercises and simulations that provide firsthand experience with security challenges. Connect security investments to business objectives like customer trust, regulatory compliance, and competitive advantage rather than framing security purely as risk reduction. When executives understand security as business enabler rather than cost center, sustainable funding and support become more likely.
Practical Starting Points for Your DevSecOps Journey
Beginning DevSecOps integration can feel overwhelming given the breadth of practices, tools, and cultural changes involved. However, successful transformation doesn't require simultaneously implementing every practice. Strategic starting points provide foundation for progressive improvement while delivering early value that justifies continued investment.
🔐 Implement secret scanning as an initial step that prevents one of the most common and easily exploited vulnerabilities—credentials committed to source code repositories. Secret scanning tools integrate easily into version control systems and CI/CD pipelines, providing immediate value with minimal implementation effort. This quick win demonstrates security automation value while preventing a vulnerability class that frequently leads to breaches. Expand from basic secret detection to include detection of API keys, database connection strings, and other sensitive configuration data.
🔍 Establish dependency vulnerability scanning provides visibility into third-party component risks that represent substantial portions of modern application security vulnerabilities. Software composition analysis tools integrate with build processes and package managers, identifying known vulnerabilities in dependencies with relatively low false positive rates. This practice requires establishing policies for addressing identified vulnerabilities, including severity thresholds for blocking builds and processes for handling dependencies without available fixes. The key is starting with visibility even if initial remediation processes remain manual, then progressively automating remediation as processes mature.
📋 Create security requirements in user stories integrates security consideration into development planning rather than treating it as afterthought. Work with development teams to identify security requirements relevant to planned features—authentication requirements, data protection needs, input validation specifications—and document them explicitly in user stories. This practice makes security visible during sprint planning and creates natural opportunities for security discussions before implementation begins. Start with high-risk features that handle sensitive data or authentication, then expand to routine features as teams become comfortable with security requirements.
🛠️ Implement infrastructure-as-code security scanning catches misconfigurations before they reach deployed environments. These tools analyze Terraform, CloudFormation, Kubernetes manifests, and other infrastructure definitions for security issues like overly permissive access policies, unencrypted storage, and publicly exposed services. Integration into CI/CD pipelines provides automated enforcement that prevents configuration drift and ensures consistent security across environments. Begin with detecting critical misconfigurations that could lead to data exposure, then expand to include compliance requirements and best practices.
👥 Establish cross-functional security forums creates communication channels that break down silos and build shared understanding. Regular meetings where development, security, and operations teams discuss security topics, share challenges, and collaborate on solutions foster relationships that support security integration. These forums shouldn't focus exclusively on problems; celebrating security wins and sharing success stories builds positive momentum. Start with monthly meetings and adjust frequency based on engagement and value, ensuring meetings remain valuable rather than becoming obligatory time sinks.
Sequencing Implementation for Maximum Impact
After establishing initial practices, sequence additional DevSecOps capabilities based on your specific risk profile and organizational context rather than following generic maturity models. Assess where your greatest security risks and friction points exist, then prioritize practices that address those specific challenges. Organizations with significant legacy code might prioritize runtime protection over static analysis, while organizations building new applications benefit from comprehensive pre-production testing. Compliance-driven organizations might emphasize continuous compliance monitoring, while startups prioritize rapid feedback mechanisms that maintain development velocity.
Avoid attempting comprehensive implementation across all applications simultaneously. Instead, identify pilot applications that represent realistic complexity but have teams open to experimentation and change. Use these pilots to refine practices, identify challenges, and demonstrate value before broader rollout. Learn from pilot experiences to improve implementation approaches, documentation, and support processes before scaling to additional teams. This progressive approach builds organizational capability and confidence while managing change impact.
How long does DevSecOps implementation typically take?
DevSecOps implementation timelines vary significantly based on organizational size, existing practices, and transformation scope. Initial practices like secret scanning can deploy in weeks, while comprehensive cultural transformation typically requires 12-24 months. Rather than viewing DevSecOps as a project with defined endpoints, treat it as continuous improvement where capabilities progressively mature. Focus on demonstrating value within the first quarter through quick wins, then build momentum for sustained transformation.
What are the most common reasons DevSecOps initiatives fail?
DevSecOps failures typically stem from cultural resistance rather than technical challenges. Common failure patterns include treating security as purely technical problem without addressing organizational culture, implementing tools without adequate training and support, creating security processes that significantly slow development without clear value, lacking executive support when initiatives face resistance, and attempting comprehensive transformation without demonstrating early value. Success requires balancing technical implementation with cultural change and maintaining focus on enabling development rather than simply enforcing restrictions.
How do we handle security findings that would block urgent releases?
Establish clear policies for security exception processes that balance security risk with business needs. Critical security issues should block releases with rare exceptions requiring executive approval and documented risk acceptance. Lower-severity findings might generate tracked remediation commitments without blocking immediate releases. Implement compensating controls like enhanced monitoring or restricted access when vulnerabilities must reach production before remediation. The key is making exception processes transparent and tracked rather than allowing security bypasses to become routine and invisible.
Should we build or buy DevSecOps tooling?
Most organizations benefit from commercial tools for core security capabilities like vulnerability scanning, where specialized vendors invest heavily in vulnerability databases and detection techniques. Consider building custom tools for organization-specific needs like policy enforcement, workflow integration, or reporting that commercial tools don't address well. Evaluate build-versus-buy decisions based on whether capabilities represent competitive differentiators, ongoing maintenance capacity, and total cost including implementation and operation. Avoid building tools primarily to avoid licensing costs without accounting for development and maintenance expenses.
How do we measure DevSecOps ROI to justify continued investment?
Measure DevSecOps ROI through multiple lenses including risk reduction metrics like decreasing vulnerability counts and severity trends, efficiency improvements like reduced remediation time and fewer production security incidents, velocity metrics demonstrating maintained or improved deployment frequency despite added security controls, and compliance benefits like reduced audit findings and faster compliance verification. Quantify avoided breach costs using industry benchmarks for incident costs in your sector. Connect security improvements to business outcomes like customer trust, competitive advantages from security certifications, and reduced insurance premiums. Combine quantitative metrics with qualitative benefits like improved team confidence and reduced security-related stress.
What skills do team members need for effective DevSecOps?
Effective DevSecOps requires T-shaped skills where team members have broad understanding across security, development, and operations with deep expertise in their primary domain. Developers need security fundamentals including common vulnerability patterns, secure coding practices, and basic threat modeling. Security professionals require understanding of modern development practices, CI/CD pipelines, and infrastructure-as-code. Operations teams benefit from security monitoring and incident response knowledge. Rather than expecting everyone to become security experts, focus on building sufficient shared knowledge that teams communicate effectively and appreciate security implications of their decisions. Invest in continuous learning through training, conferences, and dedicated learning time.