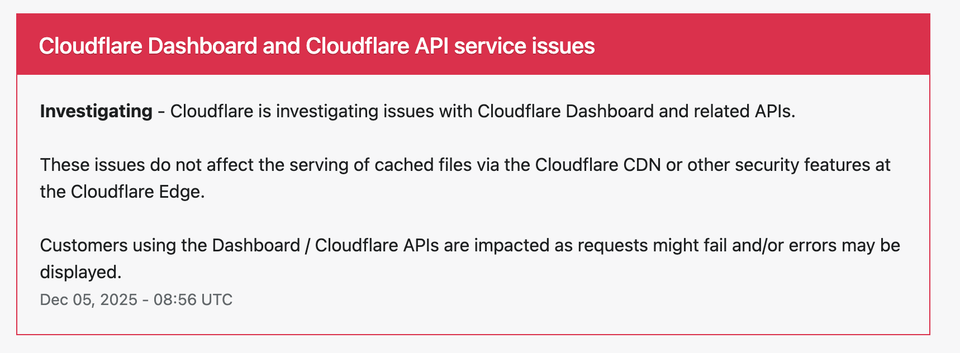
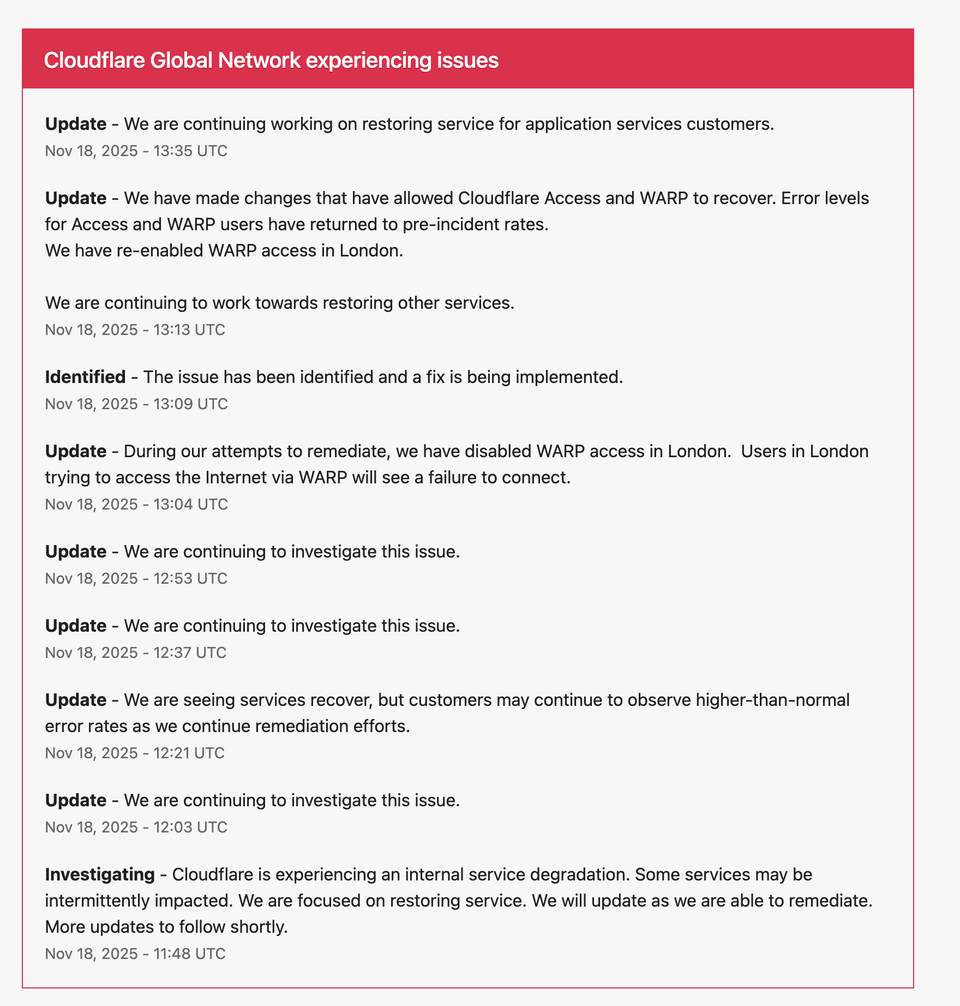
⚙️ AWS US-EAST-1 Outage: Full Technical Breakdown of Impacted Services
The disruption began with a DNS resolution failure, escalated into EC2 internal network issues, and peaked when an internal subsystem monitoring the health of AWS load balancers malfunctioned — causing false health signals and throttled instance launches.

Date: October 20, 2025
Region: US-EAST-1 (N. Virginia)
Severity: 🔴 Major Disruption → 🟡 Partial Recovery
Tags: AWS, Lambda, EC2, Load Balancer, DynamoDB, CloudFront, Networking, System Reliability, DevOps, Incident Analysis
📍 Executive Summary
On October 20, 2025, Amazon Web Services (AWS) faced a multi-layered infrastructure failure in its US-EAST-1 region, impacting over 80 individual services.
What began as a DNS resolution error rapidly evolved into a network connectivity issue caused by an internal load balancer health monitoring subsystem malfunction.
The outage disrupted essential components of AWS’s cloud ecosystem — from compute and storage layers to machine learning, security, and developer tools.
This report provides a deep-dive analysis of each impacted technology and how interdependencies amplified the incident’s scope.
📊 AWS US-EAST-1 Outage Impact Matrix (October 20, 2025)
| Category | Service / Technology | Impact Level | Issue Description | Status / Recovery Time (PDT) |
|---|---|---|---|---|
| 🖥️ Compute | EC2 (Elastic Compute Cloud) | 🔴 Major | Instance launches throttled due to internal load balancer health subsystem failure. | ✅ Stabilized by 10:45 AM |
| AWS Lambda | 🟠 High | Function invocation errors caused by internal subsystem outage and SQS event delay. | 🟡 Partial recovery by 10:30 AM | |
| ECS / EKS | 🟠 High | Container deployments stalled due to ELB and networking instability. | ✅ Recovered by 9:45 AM | |
| 💾 Databases & Storage | DynamoDB | 🔴 Major | DNS resolution failure for API endpoints in US-EAST-1. | ✅ Fully mitigated by 3:35 AM |
| RDS (Relational DB Service) | 🟡 Moderate | Connection timeouts and latency due to EC2 dependency. | ✅ Restored by 8:00 AM | |
| Amazon S3 | 🟢 Minor | Indirect latency due to EC2 networking bottlenecks. | ✅ Operational | |
| Redshift / Glue | 🟠 High | Interrupted ETL jobs and delayed analytics queries. | ✅ Recovered by 9:00 AM | |
| 🌐 Networking & Delivery | Elastic Load Balancing (ELB) | 🔴 Critical | Root cause: internal subsystem monitoring load balancer health malfunctioned. | ✅ Patched by 10:03 AM |
| Amazon CloudFront | 🟠 High | Content delivery errors (503/504) due to backend API instability. | ✅ Recovered by 9:15 AM | |
| Amazon Route 53 | 🟢 Minor | Internal DNS propagation delay for DynamoDB endpoints. | ✅ Fixed by 3:35 AM | |
| VPC / PrivateLink | 🟠 High | Internal traffic congestion and packet loss. | ✅ Resolved by 8:04 AM | |
| 🔐 Security & Access | IAM (Identity and Access Management) | 🟡 Moderate | Policy update delays due to DynamoDB dependency. | ✅ Normalized by 5:00 AM |
| Secrets Manager / KMS | 🟡 Moderate | Delayed secret retrieval and encryption key access. | ✅ Recovered by 6:00 AM | |
| 📡 Integration & Messaging | SQS (Simple Queue Service) | 🟠 High | Message processing backlog; Lambda polling delays. | ✅ Fully recovered by 5:10 AM |
| SNS (Simple Notification Service) | 🟢 Minor | Slight delay in cross-region message delivery. | ✅ Stable | |
| EventBridge / CloudTrail | 🟡 Moderate | Delayed event logging and delivery. | ✅ Operational by 5:48 AM | |
| 📊 Monitoring & Management | CloudWatch | 🟡 Moderate | Lag in telemetry updates and missing metrics data. | ✅ Auto-backfilled by 8:30 AM |
| CloudFormation | 🟠 High | Stack creation/update failures due to EC2 API errors. | ✅ Restored by 9:20 AM | |
| 🤖 Machine Learning & AI | SageMaker | 🟡 Moderate | Training job delays due to EC2 node provisioning issues. | ✅ Stable by 10:00 AM |
| Polly / Transcribe / Comprehend | 🟢 Minor | Sporadic latency in service responses. | ✅ Operational | |
| 🔧 Developer Tools | CodeBuild / CodePipeline | 🟠 High | Build failures and delayed CI/CD jobs due to API timeouts. | ✅ Stable after 9:00 AM |
| Cloud9 / SDKs / CLI | 🟢 Minor | Temporary region connectivity errors. | ✅ Recovered early morning |
🧩 Summary Insights
- Total Impacted Services: 82
- Root Cause: Internal subsystem failure monitoring Load Balancer Health
- Primary Affected Layers: EC2 Networking, DNS, Lambda Invocation
- Duration: ~10 hours total impact (12:11 AM – 10:45 AM PDT)
- Peak Severity Window: 2:00–8:45 AM PDT
💡 Observations
- The load balancer health subsystem acted as a central failure point across EC2, Lambda, and internal APIs.
- DNS recovery was fast (<4 hours), but network revalidation and Lambda subsystem fixes extended recovery.
- Multi-AZ flexibility mitigated the worst customer impact for auto-scaling and high availability workloads.
🔗 References
📘 AWS Service Health Dashboard
📰 Dargslan Publishing – Full AWS US-EAST-1 Outage Analysis
💡 Learn Cloud Resilience Engineering – dargslan.com
🖥️ Compute Layer: EC2, Lambda, ECS, and Fargate
Amazon EC2 (Elastic Compute Cloud)
EC2 forms the backbone of AWS infrastructure — powering web servers, microservices, and backend APIs.
During the incident, EC2 instance launches were throttled due to false health signals from the load balancer subsystem.
- Impact: “Insufficient Capacity” and “Launch Failure” errors across multiple AZs.
- Resolution: Gradual restoration and validation of EC2 launches by zone (8:43–10:45 AM PDT).
“We recommend EC2 Instance launches that are not targeted to a specific AZ so that EC2 has flexibility in selecting the appropriate zone.”
AWS Lambda
Lambda, AWS’s serverless compute platform, experienced invocation failures.
Because Lambda internally depends on load balancer health checks for scaling and event dispatch, these failures caused function timeouts and retries.
- Impact: Function invocation errors and delayed Event Source Mappings (SQS, DynamoDB Streams).
- Resolution: Engineers validated recovery by redeploying fixes to internal health subsystems.
“Lambda is experiencing function invocation errors because an internal subsystem was impacted by the network load balancer health checks.”
Amazon ECS & EKS (Containers and Kubernetes)
Both Elastic Container Service and Elastic Kubernetes Service rely heavily on EC2 networking and ELB (Elastic Load Balancing).
As ELB health checks degraded, containerized workloads faced scaling latency and intermittent deployment failures.
- Impact: Pods and containers stuck in “Pending” or “Provisioning” state.
- Resolution: Restored through load balancer subsystem reconfiguration and API recovery.
💾 Data Layer: DynamoDB, RDS, Redshift, S3
Amazon DynamoDB
The initial domino that triggered the event — DynamoDB’s API endpoints failed DNS resolution.
This affected multiple downstream services, including IAM updates and DynamoDB Global Tables.
- Impact: High error rates and failed API calls between 12:11–3:00 AM PDT.
- Resolution: DNS fixed by 3:35 AM PDT; global synchronization restored.
Amazon RDS (Relational Database Service)
RDS instances in the affected region could not connect to EC2 or Lambda due to network disruptions.
Replication and automatic failover events were delayed but not lost.
- Impact: Temporary query latency and connection retries.
- Resolution: Stabilized once EC2 internal networking was restored.
Amazon Redshift and Glue (Analytics Services)
Data warehouse and ETL jobs failed mid-run due to API timeout errors.
Jobs relying on S3 inputs or Lambda triggers paused automatically to prevent data loss.
- Impact: Interrupted ETL pipelines, stuck query executions.
- Resolution: Recovered after API revalidation around 9:00 AM PDT.
Amazon S3 (Simple Storage Service)
While S3 itself remained stable, any compute or analytics service depending on S3 over EC2 networking experienced latency.
- Impact: Slower access to S3 buckets from Lambda and ECS.
- Resolution: Recovered after EC2 load balancer subsystem restoration.
🌐 Networking and Delivery Layer: ELB, CloudFront, Route 53, VPC
Elastic Load Balancing (ELB)
At the heart of the incident: AWS’s internal subsystem monitoring load balancer health became unstable.
This caused false positives marking healthy targets as degraded.
- Impact: Throttled instance launches, API connectivity drops.
- Resolution: Subsystem patched and validated zone-by-zone by 10:03 AM PDT.
Amazon CloudFront
As global traffic routed through impacted endpoints, CloudFront observed increased error rates in content delivery for US-based users.
- Impact: Intermittent 503/504 gateway errors on cached content.
- Resolution: Resolved automatically as network latency improved.
Amazon Route 53
While Route 53 itself was stable, internal DNS propagation errors from EC2’s private zone caused misrouting of DynamoDB endpoints.
- Impact: Delayed DNS resolution and name server lookups.
- Resolution: Fully mitigated by 3:35 AM PDT.
Amazon VPC and PrivateLink
VPC connectivity, PrivateLink tunnels, and NAT gateways experienced high packet loss due to network congestion.
- Impact: Cross-service communication failures inside private subnets.
- Resolution: Traffic normalization by 8:04 AM PDT.
🛡️ Security and Access Layer: IAM, Secrets Manager, KMS
AWS IAM (Identity and Access Management)
IAM updates and new user provisioning were delayed due to DynamoDB API dependency (used internally for policy replication).
- Impact: Temporary failure to apply new IAM roles or permissions.
- Resolution: Recovered as DynamoDB stabilized.
AWS Secrets Manager & KMS
Secrets retrieval from KMS-backed vaults was slowed down, leading to function startup delays in Lambda and ECS.
- Impact: Delayed encryption/decryption during authentication.
- Resolution: Fixed after IAM and DynamoDB recovery.
📡 Messaging and Integration Layer: SQS, SNS, EventBridge, CloudTrail
Amazon SQS & SNS
Message delivery delays occurred due to Lambda polling and EC2 networking issues.
Event-driven applications like billing and notification systems saw lagged message propagation.
“We confirm that we have now recovered processing of SQS queues via Lambda Event Source Mappings.”
- Impact: Lag in SQS → Lambda workflows.
- Resolution: Full processing resumed by 5:10 AM PDT.
Amazon EventBridge & CloudTrail
Event-driven monitoring pipelines briefly failed to record new events.
CloudTrail logs accumulated backlog, later cleared during the recovery phase.
- Impact: Delayed event logging and automation triggers.
- Resolution: Normalized delivery confirmed by 5:48 AM PDT.
🧠 Machine Learning and AI Layer
Amazon SageMaker
Training jobs relying on EC2 compute nodes paused automatically when EC2 instance launches failed.
- Impact: Delayed model training and batch inference jobs.
- Resolution: Automatic restart after instance revalidation.
Amazon Polly, Transcribe, and Comprehend
These services, dependent on load-balanced compute clusters, experienced sporadic latency but no major data loss.
🧩 Developer and Management Tools
AWS CloudFormation
Infrastructure-as-Code (IaC) deployments failed to complete due to EC2 API timeouts.
- Impact: Stack creation and updates hung in “IN_PROGRESS.”
- Resolution: Recovered as EC2 and IAM stabilized.
AWS CloudWatch
Metrics ingestion delayed by several hours, affecting dashboards and alarms.
- Impact: Gaps in telemetry for affected resources.
- Resolution: Backfilled automatically after API recovery.
🧱 Internal Dependencies and Cascading Effects
The outage demonstrated the deep coupling between AWS’s internal services:
- DNS failures disrupted API routing.
- EC2 network instability broke control plane communication.
- Load balancer health subsystem failure propagated false degradation signals.
Each dependency amplified the next — a cascading effect seen even in highly redundant systems.
🧩 Engineering Takeaways
- Build for graceful degradation.
Architect workloads that can handle partial service failure without full downtime. - Distribute across multiple regions.
Multi-region failover remains essential for production-grade resilience. - Monitor AWS dependencies.
Use synthetic testing from multiple regions to detect external dependency failures early. - Cache critical data locally.
Reduce reliance on external calls during upstream API instability.
🧭 Conclusion
The October 20, 2025 AWS US-EAST-1 outage was a complex, multi-phase event involving DNS, network, and load balancing systems.
Despite the vast scale, AWS engineers demonstrated resilience through real-time diagnostics, transparent communication, and controlled recovery.
“Recovery efforts are progressing, and most AWS services are now stable.”
This incident serves as a case study in cloud fault tolerance, system observability, and dependency management — crucial lessons for every DevOps and cloud engineering team.
📘 Full Incident Log: AWS Service Health Dashboard
🔗 Extended Analysis: Dargslan Publishing AWS US-EAST-1 Report
💡 Learn Cloud Reliability Engineering: dargslan.com